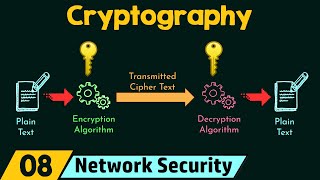
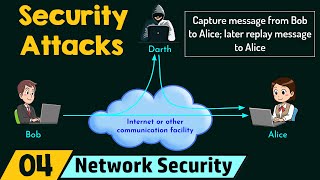
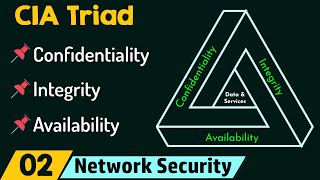
Network Security Model
Вставка
- Опубліковано 23 жов 2024
- Network Security: Network Security Model
Topics discussed:
1) Explanation of the need for a network security model.
2) Four major tasks for designing a model for network security.
3) Explanation of the need for network access security model.
4) Role of a gatekeeper function to protect the information systems.
Follow Neso Academy on Instagram: @nesoacademy (bit.ly/2XP63OE)
Contribute: www.nesoacademy...
Memberships: bit.ly/2U7YSPI
Books: www.nesoacademy...
Website ► www.nesoacademy...
Forum ► forum.nesoacad...
Facebook ► goo.gl/Nt0PmB
Twitter ► / nesoacademy
Music:
Axol x Alex Skrindo - You [NCS Release]
#NetworkSecurityByNeso #Cryptography #NetworkSecurity #NetworkSecurityModel






It is so sweet like a grand mother telling a very beautiful story to the kid who is curiously listening.. kudos to the great teacher who is telling the niche with all zeal and enthusiasm.. we need teachers like this in all schools and colleges.
pooyi podukora pukaa
Actually I am searching for this topic at the correct time u have uploaded this thank u once again😍
Thank you so much sir ❤
Please draw some annotations on the PPT, otherwise it is hard to concentrate
Really a good session sir, thank you
On one of the slides you had the item "Design an algorithm". Did you actually do this designing in the rest of the presentation? I seem to have missed it.
Furthermore, it is common knowledge in the IT security community that you should not design your own cryptographic algorithms, you should rather use the established ones. Would it be more appropriate to say "Choose an algorithm" instead?
Good explain
Interesting
Please upload some videos on project related topics based on security!!
Nice explanation .
Thank u sir
I want to know is the learning courses we are supposed to learn week 8
Thank you sir.
Amazing lecture sir
Impressive video lecture
Tq ,sir
Nice 👍 thanks 👍😊
Excellent.
Thank you so much
Tq sir
Excellent
When will u upload the next video.plz make it soon sir.
Starts at 0:34
How can a gate keeper identify a legitimate and non legitimate user
Sir slides???
👍👍
Koncham mellaga cheppu ra
🤣😆
Speed thakuva petti vinu😂
Actually it is boring