Understanding Symmetric Keys: Unlocking Secrets Step by Step Explained
Вставка
- Опубліковано 18 лют 2024
- Discover the fascinating world of symmetric key encryption and its inner workings in this enlightening video. Join us as we delve into the concept of symmetric key encryption, which is extensively used to secure data transmission and protect sensitive information. Understand how symmetric key encryption operates, its advantages, and the essential components involved. Explore the intricacies of key generation, encryption, and decryption processes, and grasp the importance of confidentiality in data security. Enhance your knowledge of cryptography and uncover the power of symmetric key encryption with our comprehensive guide. Watch now and become proficient in the fundamentals of symmetric key encryption!
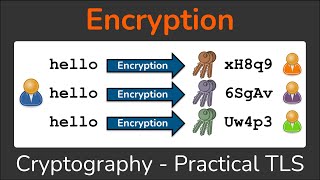
A symmetric key, also known as a secret key or private key, is a cryptographic key used in symmetric-key cryptography. In this cryptographic system, the same key is used for both encryption and decryption of data.
Here's how it works:
Encryption: The sender uses the symmetric key to encrypt the plaintext data, turning it into ciphertext.
Decryption: The recipient then uses the same symmetric key to decrypt the ciphertext, converting it back to the original plaintext.
The key characteristic of symmetric-key cryptography is that both parties involved in the communication must possess the same secret key. This key needs to be kept confidential between the communicating parties to ensure the security of the encrypted data.
Symmetric key algorithms are generally fast and efficient for encrypting large amounts of data. However, the main challenge with symmetric-key cryptography is securely sharing the secret key between communicating parties. If an attacker intercepts the key during transmission, they can decrypt the encrypted messages. This problem is typically addressed through secure key exchange protocols or by using asymmetric cryptography for initial key exchange followed by symmetric cryptography for the bulk of the communication.
#symmetrickeyencryption, #encryptionexplained, #cryptography101, #datasecurity, #symmetrickeystrength, #encryptionalgorithms, #confidentiality, #symmetrickeygeneration, #encryptionprocess, #securedatatransmission