
- 7
- 208 915
Chalk Talk
Приєднався 9 чер 2022
Math, computer science, physics, etc.
Made by Kelsey Houston-Edwards
www.kelseyhoustonedwards.com
Made by Kelsey Houston-Edwards
www.kelseyhoustonedwards.com
The Rational Numbers Are Not So "Rational" | Everywhere but Nowhere, Part 1
The rational numbers are not so... "rational". (Yes, yes, I know: The name rational comes from ratio - they're the ratios of whole numbers. The word rational has a second meaning. We're playing with that here.)
________________
Timestamps:
0:00 Intro
0:39 Everywhere
2:09 But Nowhere
_______________
A Hierarchy of Infinites | PBS Infinites Series -- ua-cam.com/video/i7c2qz7sO0I/v-deo.html
_______________
Created by Kelsey Houston-Edwards
www.kelseyhoustonedwards.com
________________
Timestamps:
0:00 Intro
0:39 Everywhere
2:09 But Nowhere
_______________
A Hierarchy of Infinites | PBS Infinites Series -- ua-cam.com/video/i7c2qz7sO0I/v-deo.html
_______________
Created by Kelsey Houston-Edwards
www.kelseyhoustonedwards.com
Переглядів: 57 253
Відео
Learning with errors: Encrypting with unsolvable equations
Переглядів 37 тис.Рік тому
Learning with errors scheme. This video uses only equations, but you can use the language of linear algebra (matrices, dot products) to discuss lattices and learning with errors. Check out the resources below for more information. Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com) Sponsored by Wire (www.wire.com) Post-Quantum Cryptography: ua-cam.com/video/_C5dkUiiQnw/v-deo.html L...
Lattice-based cryptography: The tricky math of dots
Переглядів 59 тис.Рік тому
Lattices are seemingly simple patterns of dots. But they are the basis for some seriously hard math problems. Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com) Sponsored by Wire (www.wire.com) Post-Quantum Cryptography: ua-cam.com/video/_C5dkUiiQnw/v-deo.html Learning with Errors: Coming January 5, 2023 Timestamps 0:00 - Post-quantum cryptography introduction 0:58 - Basis vectors...
Post-quantum cryptography: Security after Shor’s algorithm
Переглядів 32 тис.Рік тому
What’s the current status of the NIST Post-Quantum Cryptography Standardization? Find out here: csrc.nist.gov/Projects/Post-Quantum-Cryptography Created by Kelsey Houston-Edwards (www.kelseyhoustonedwards.com) Sponsored by Wire (www.wire.com) Lattice-Based Cryptography: ua-cam.com/video/QDdOoYdb748/v-deo.html Learning with Errors: Coming Jan 5, 2023 Timestamps 0:00 - National Institute of Stand...
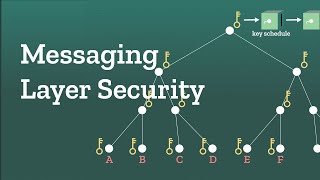
Messaging layer security: Encrypting a group chat
Переглядів 12 тис.2 роки тому
How do you keep the messages in a group chat secure? Messaging layer security (MLS). The Double Ratchet algorithm provides end-to-end encryption for text messages between two people. But securing a group chat is much harder. MLS is the first standardized multi-party “key exchange” - a protocol for communication among groups of people or devices. Resources: Video on the Double Ratchet algorithm:...
Double ratchet algorithm: The ping-pong game encrypting Signal and WhatsApp
Переглядів 15 тис.2 роки тому
How do text messaging services like Signal and WhatsApp keep your text messages secure? The Double Ratchet algorithm. Let’s say Alice wants to send Bob an end-to-end encrypted message. She uses a key to lock up the message and Bob uses the same key to unlock the message. But what if they want to send a bunch of messages back and forth? Using the same key the whole time is not very secure. It wo...





Wait... Infinite Series host is back?
Can you provide context on how a brute force attack to these solutions compares to RSA? And how much compute per byte is required to encrypt/decrypt (with key) compared to RSA? There is an assumption these are quantum-proof, but how do you know? How many qubits will it take, and how many might be in a future quantum computer? What if the future quantum computer has 100 billion qubits?
The photograph of this video is incredible, the colors are so comfortable, the girl is pretty, the voice is good. Feels really like dark academia
Aha, so infinite DOES equal zero!
Smart and sexy? 😭
Since quantum computers are not good in precise floating point arithmetics lets use floating point functions for the new encryption algorithm, at least in parts
Glad I found you today. I didn't know you had your own channel. Did you finish your heat equation research?
What's to stop me taking choice linear combinations of the public basis so that it spans the space more efficiently? I understand it would be a large set of vectors, but it doesn't seem like a problem whose complexity grows fast
I guess an understanding of Diffie-Hellman would be a helpful pre-req here.
Very well explained. Thank you.
Very useful information. Is wire just like RCS?
I thought paradox was just self-contradictory ideas. I'm glad I did a google search first. What was the most paradoxical paradox?
Oh my god Kelsey, you just appeared in my feed. I am so so so happy that you are back! I was really sad when you left PBS Infinite Series! My best wishes for your channel!
5:11 Throwing a dart at the reals has always intrigued me. I'm probably wrong, or going by the wrong definition of impossible, but I feel like it IS impossible to hit a rational. I think of it like this: The decimal expansion of the dart position is countably infinite. As the position was chosen at random, it is effectively like rolling a 10-sided die countably infinite times. To be equal to a rational means that at some point, the sequence of die rolls needs to start repeating. And it needs to repeat infinitely! That feels impossible. And considering again rolling a 10-sided die countably infinite times, it seems intuitive that you would always end up with a sequence that has no sort of pattern to it, so that the only way to express the number would be to somehow write down an infinite list of every single digit. i.e. a non computable number (I think).
ara you really sure that rational means 'rational' ?
What a terrific video, I’m so glad to have come across someone who explains complex things with such clarity
what this type of lwe is called?
Very well produced. Thank you for posting.
Awesome content. Wish you publish more videos on channel!
I think it is natural for someone (who have never seen or understand why natural numbers are countable) to ask why you count the list of natural numbers from the top left corner and then snake down the way that you showed it. Beginners may not understand why, and it makes a huge difference if you don't count it that way. I was one of those beginners when I took Real Analysis at UC Berkeley. I asked my professor Jacob Feldman why we had to count that way. His response was very simple; "If you don't, you will never get to the next line or next column" In other words, you will forever stay on the first row (if you start counting the first row) or you will forever stay on the first column (if you start counting the first column).
Why do irrational numbers take up more than 0 space? Aren't they also just a single point?
I think the people answering 99 are doing so by assuming that the 98% you mentioned was the water percentage before dehydration.
so in math terms: before sun: 1% of x = 1kg (solving for x) or 100 kg after sun: 2% of x = 1 kg (solving for x) or 50 kg
The most beautiful thing in mathematics is the moments when something which once mystified you makes you say “well how could it possibly be any other way?”
Monty Hall comes to mind.
You are very good at what you do, conveying something subtle and interesting/meaningful.
Isn't 0 + 0 + ... Infinitely many times an 'indeterminate form' ?
You are Cute
Wow I thought this would be a fluff piece when I clicked but this actually went unnecessarily hard lol, +1 subscriber! As a math enthusiast myself, I would’ve liked some more specific mathematics beyond the exponent rules but nonetheless very well made video!
Very well made video. Great sound, excellent visuals, and extremely well expressed explanations. A joy to watch. Thank you so much!!
The “ratio” in rational should tell you that it’s a literal ratio, not something literally sensible.
The fraction of dart throws on the real number line that land on rational numbers approaches 0 as the number of throws approaches infinity.
Rational numbers are countably infinite ...aleph null.
Nicely done! When you say, "The measure of the point must be 0.", I think it is better to say, "The length of the point must be 0.", since it is easier for students to understand "measure"ment with "units" and you use interval theory to explain this "measure", and then follow up by stating that measurement does not have to include units here. I use to show my students the idea of (although very limited) creating irrational numbers using the square root of any number that is "not" a perfect square, and my extending idea that any repeating sequence of digits (at first more easily understood for values less than one), such as .313131... can be immediately converted to a rational number, finding the last digit of the first set of repetitive values (31 <-- the 1 in .31...) and putting the decimal location in the denominator (1 is in the 100ths place, so x/100), subtracting one from the denominator (x/99) and then writing the repeating digit sequence on top (31/99) = .313131, and some other examples .443... = 443/999, .003450034500345... = 345/99999, 2.74... = [(2x99 "or" 200-2)+74]/99 = 272/99. Note that if we add just 1 to the numerator of the last value we get 1 added to the repetitive sequence in "that 100ths position", i.e. 273/99 = 2.7'5'7'5'... and 274/99 = 2.7'6'7'6'... or if we subtract the whole number from the "obvious" 274 numerator in the first example (2.74... ) we get the correct numberator 272/99=2.7474...(!) etc.. Do you like these ideas? Your explanation should be the cornerstone of a description for beginning interval theory(-ries).
wow thats very interesting 😊
At some point, it would probably be worth mentioning that the word “rational” is not used in the sense of sensible to mathematicians. Mathematicians mean to imply that a rational number is the ratio of two numbers.
At some point, it would probably be worth mentioning that the word “rational” is not used in the sense of sensible to mathematicians. Mathematicians mean to imply that a rational number is the ratio of two numbers.
this video helped me so much with my discrete mathematics exam! thank you!
That'd be why rational numbers make good interval endpoints?
Rock Chalk Chalk Talk! I’m from Kansas 🦜
All those smarmy and unctuous comments are unbearable
Glad to see you are back. Keep up the good work please!
So the rational numbers are countable and have length zero? What then is the total length of all countable numbers together?
So 0% is not quite zero but as near to zero as you can get. as both rational and irrational exist
You say "number line" like it's no big deal, but it's the real numbers that are strange. For one thing, a real number can contain an infinite amount of information.
Fir God' sake, what's in a name?
Hi Kelsey, Congrats on your PhD! I recently discovered your work with PBS Infinite Series and I really loved your explanations, so I found your current YT channel. Could you possibly make a video on undirected and directed graphical models? I am particularly interested in these concepts within the context of machine learning. It would help me a lot with some self-studying I’m doing for a course (PGM). Thank you!!!
This is so depressing. I clicked in the hope of some interesting perspective, but the talk is about decimal numbers, which are not at all rational, and don't even exist in pure math, because they can't be given a rigorous arithmetic (unlike continued fractions). Decimals do have some handy pragmatic properties in applied math, but that's an other story (Stevin was an engineer).
What do you think then is the relation between decimals or rationals of your choosing and probability theme?
@@skalderman As for probability theory, I think that's just unnecessary and confusing sophistry attached to theory of fractions. Kolmogorov's unitarity axiom is already naturally included in Stern-Brocot construction of fractions. Little known fact that sum of simplicities 1/ab of each new row of mediants a/b adds up to 1/1, but still a fact. Stern-Brocot algorithm is holistic top down nesting algorithm, while what are currently called rationals is based on a bottom-up additive algorithm, which does not allow to write fractions of the type 1/0 etc. n/0. After I found out that continued fractions can be written as zig-zag paths along the binary tree nested in Stern-Brocot structure, I lost all interest in decimals, and in my view in pure math they simply don't exist. The supposedly infinite string 0,333... cannot be transformed back to the fraction 1/3, so why bother with an ugly and absurdly non-computational pseudorepresentation in pure math, especially when we have continued fractions and their Gosper arithmetic? Let engineers do their applied math as they please, but that's no reason to try to pollute pure math with what are absurdities from our more rigorous perspective. Keeping pure math pure, maybe we'll come up also with genuinely constructive as well as very pragmatic algorithmic apps that benefit also engineers.
Just found your channel! 🤗 Still love to watch some of the PBS Infinite Series classics from time to time 👍
The probability of any specific number (of any type, rational, irrational, natural, etc.) is zero, without a doubt. This is why we use the concept of probability density. In practice, however, outside of Mathematics, with the limits of precision of instruments, the probability of specific values are not zero, because they end up in integrals of intervals centered on themselves. ;-)
Nice! Looking forward to seeing the next part(s). I've been wondering if reality might, in fact, be rational but not real. Maybe Kronecker had a point about man _inventing_ the reals. As with the "imaginary" numbers, the "rational" numbers seem confusingly named. They are ratios, ratio-nal numbers. 😁